This post will provide more details about Windows 10 or Windows 11 Software Update Patching Options with Intune. How do you patch Windows 10/11 devices managed with Intune? Are you interested in learning more about Intune Vs SCCM And WSUS Vs WUfB Patching Method Differences?
Microsoft Software Update Patching process for Intune admins. Intune helps configure Windows Update for Business (WUfB) policies to patch. This is the simplified patch management using Intune and WUfB.
Latest Post for Monthly Patching using Intune – Windows 11 Monthly Patch Deployment Using Intune HTMD Blog (anoopcnair.com)
The latest update guide for Intune monthly patching is available in the following Cloud PC Monthly Patching Process Using Intune. You can also configure Windows 10 and 11 Feature Update using Intune policies.
Table of Contents
Intune Monthly Patching Guide Software Update Patching Options with Intune WUfB
Software update deployment with IntuneMicrosoft Intune provides Windows 10/11 Update Rings management to enable Windows as a Service via the Software Updates feature.
This enrolls a Windows PC into Windows Update for Business to manage features and quality updates the device receives and how quickly it updates to new releases. Software update deployment with Intune is straightforward. A few configuration steps, profile creation, and deployment are all done.
In this blog post, I will describe how to configure Windows update deployment through Intune on Windows 10 devices enrolled with Windows Autopilot.
Update rings are policies that you assign to groups of devices. The following video provides more details on Intune-based patching strategies. Intune Patch Management Methods for Windows iOS iPadOS macOS – Intune Design Decisions Part 7.
In the following blog post, we have explained the troubleshooting methods for identifying the issue with event logs and registry keys: https://howtomanagedevices.com/intune/2319/uninstall-windows-10-feature-update/.
Prerequisites
To use the Windows updates feature for Windows 10 devices in Intune, the following prerequisites must be fulfilled: Server Operating Systems are not supported with Intune and Windows Update for Business.
As per Microsoft, additional prerequisites to use Windows Update for Business (WUfB) are given below. This includes the licensing requirements and others.
Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
Windows Virtual Desktop Access E3 or E5
Microsoft 365 Business Premium
Additionally, devices managed by the Windows Update for Business deployment service must have the following:
Windows 10 version 1709 or later
Azure AD joined, or Hybrid AD joined
Windows 10 or Windows 11 editions installed: Pro Enterprise Education Pro for Workstations
Create a windows update policy
To create the policy for software updates, go to Microsoft Intune—Overview and Software Updates, then click on Software Updates. You will see the blade-like following.
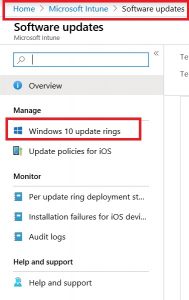
Click on Windows 10 update ring, then click on Create.
Enter the Name and Description of the Intune Patching or Software Updates policy.
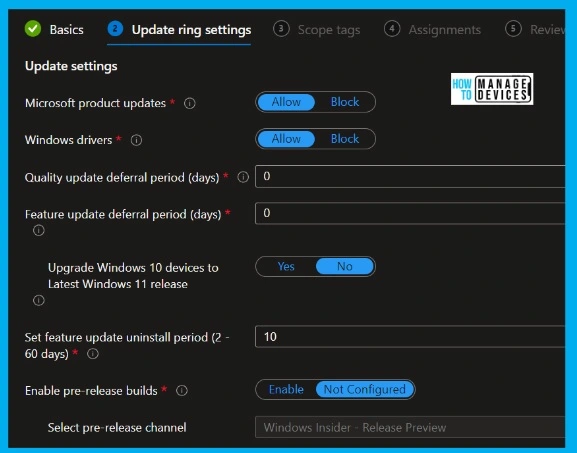
Intune Patching Update Settings
I have segregated this monthly patch policy configuration into two sections 1. Update Settings 2. User experience settings for easy understanding. This is the policy I created for the Day 0 deployment ring of Windows 11 devices.
You will see many options that need to be configured in the update settings. Microsoft removed this section about the Servicing channel from the Intune update policy.
You must select the update servicing based on your requirement and the organization’s need; here, I have chosen a semi-annual channel.
1) You need to configure several days for a quality update and feature update at different times, from how many days these updates will install after release. I would recommend using different policies with more granular control for feature updates.
- Update settings
- Microsoft product updates – Allow.
- Windows drivers – Allow.
- Quality update deferral period (days) – 0– Defer quality updates for the specified number of days for Windows 11 PCs. The allowed value is between 0-30 days.
- Feature update deferral period (days) – 0 – Defer feature updates for the specified number of days for Windows 11 PCs. The allowed value is between 0-365 days.
- Set feature update uninstall period (2 – 60 days) – 10 – This is to set the feature update to uninstall period. The allowed value is between 2-60 days.
- Upgrade Windows 10 devices to the Latest Windows 11 release – NO
- Enable pre-release builds – Enable?
- Select Pre-Release Channel – Windows Insider Channels (DEV or BETA)
User Experience Setting
User experience settings are settings you configure to improve end-users’ experience doing their day-to-day work without interruption.
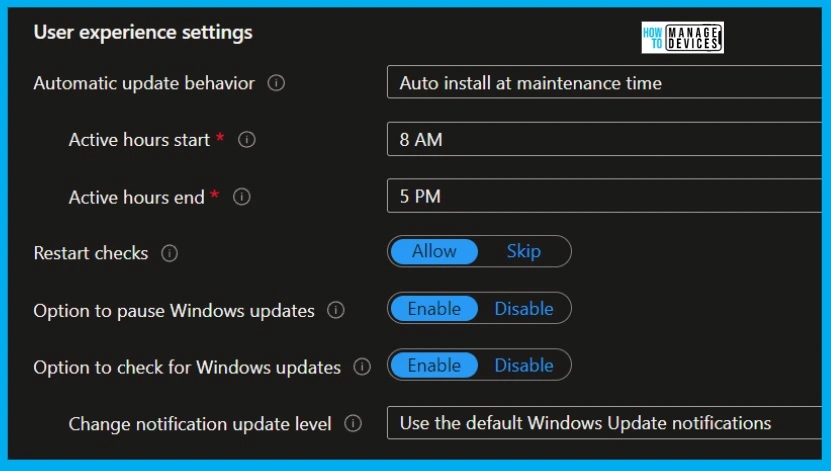
The first setting is automatic update behavior, where you configure how your devices will install updates.
It either installs automatically or notifies the users to download the updates, install updates during maintenance time, or install the updates automatically and restart the device in the scheduled time.
The next setting is to provide an active start time and active end time; these are very important to configure the maintenance window for installing updates.
Next is restart checks, which means you can configure the restart check either for the battery power up to 40% or something else; you can skip this setting.
If you want users to have to approve for computer restart post-update installation, then you can enable this setting, and the user can authorize a computer restart,
If you want to deploy updates on Windows 10 devices, configure all the settings, including servicing channel, product, and driver updates. Also, update deferral periods, user experience settings, the deadline for updates, and, most importantly, auto-reboot settings.
I would say all the settings are critical and required for all organizations, but they differ based on the security policies.
You can now configure the User Experience settings for the Windows 11 monthly patch deployment policy. These Intune policies are configured in the Intune Admin Center portal. I have not changed the settings of any of these policies for the Day 0 deployment ring.
- Automatic Update behavior -> AutoInstall at maintenance time.
- Active hours start -> 8 AM
- Active hours end -> 5 PM
- Restart checks – Allow – This policy is set to skip all checks before restart: Battery level = 40%, User presence, Display Needed, Presentation mode, Full-screen mode, phone call state, game mode etc.
- Option to pause Windows updates -Enable
- Option to check for Windows updates – Enable
- Require user approval to dismiss restart notification – No
- Remind user before required auto-restart with a dismissible reminder (hours) – The allowed number of hours, 2, 4, 8, 12, or 24 – 2 Hours.
- Remind user prior to required auto-restart with a permanent reminder (minutes) – The allowed number of minutes, 15, 30, or 60 – 30 Minutes.
- Change notification update level – Use default Windows Update notifications.
Intune Patching – Deadline Configurations
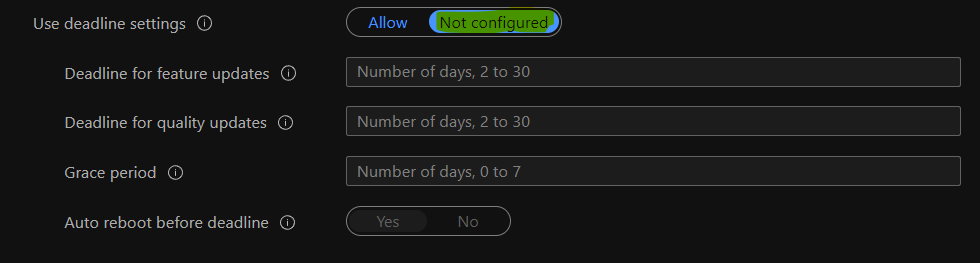
Now, you must configure the deadline settings experience for Windows 11 PCs. You have to be careful about these configuration policies because they define the restart behavior for users, reminders, etc.
I have not configured these deadline settings policies for the Day -0 deployment ring in my lab environment. However, I recommend configuring these policies according to your business requirements.
- Use deadline settings -> Not Configured
- Deadline for feature updates ->
- Deadline for quality updates ->
- Grace period –>
- Auto reboot before the deadline –
- Click on Next to continue.
Deployment of Software Updates and Patches
Let’s check the Deployment of Software Updates and Patches using Intune and Windows Update for Business. You can deploy this policy either to users or device groups. Intune has the intelligence to understand the devices assigned to a user using the lookup method.
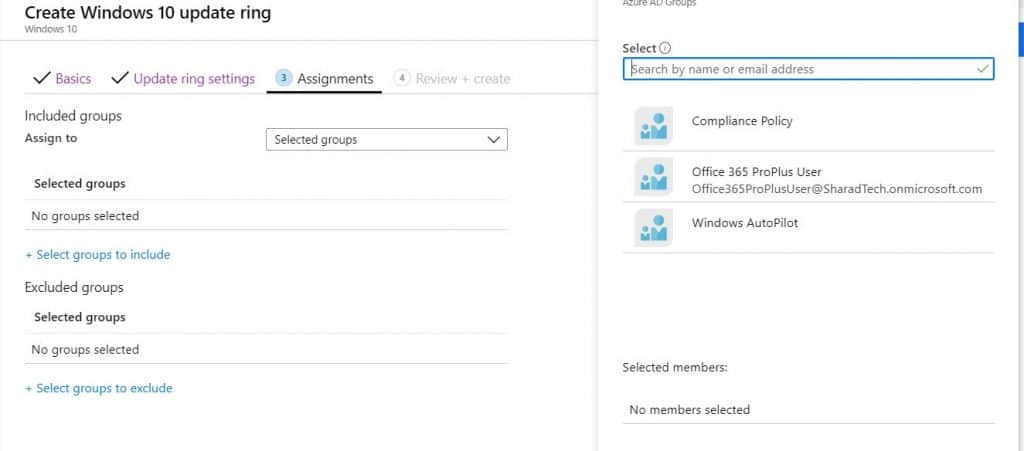
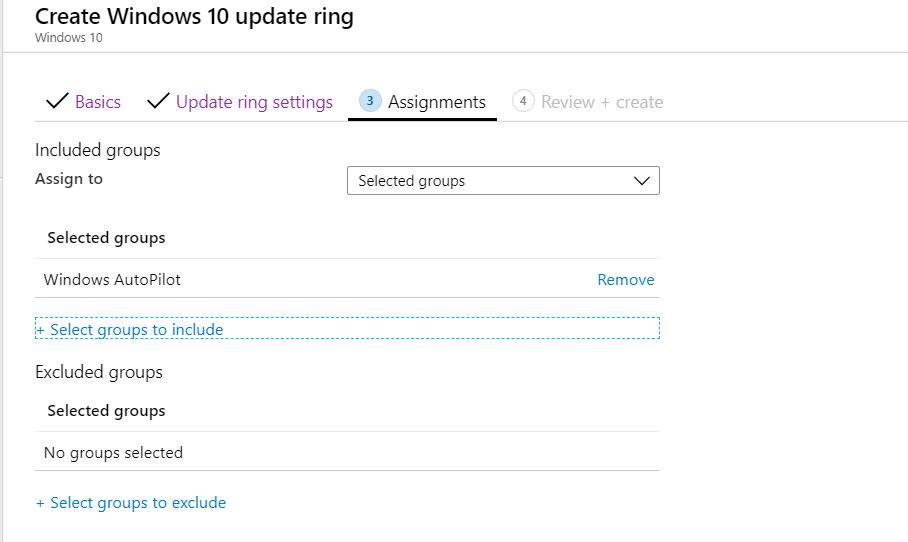
The update ring assignment is straightforward. You look in the right hand, select the group to which your Windows 10 devices are added, and update them.
I wanted to update you on all my Windows autopilot devices, so I selected the group.
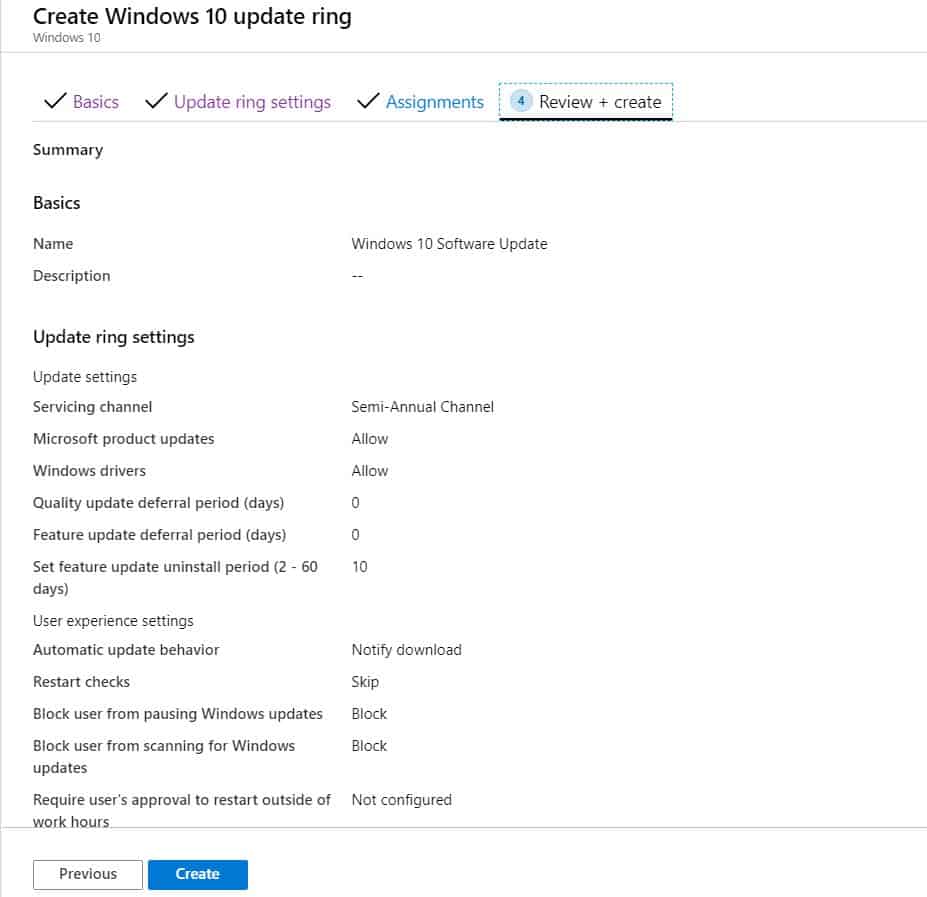
End User Experience of Intune Patching using WUfB
In the next window, review your configured settings and click on Create.
When I check my Windows 10 device and window update, I can see the policy is applied, and Windows 10 is downloading the update, which is fast,
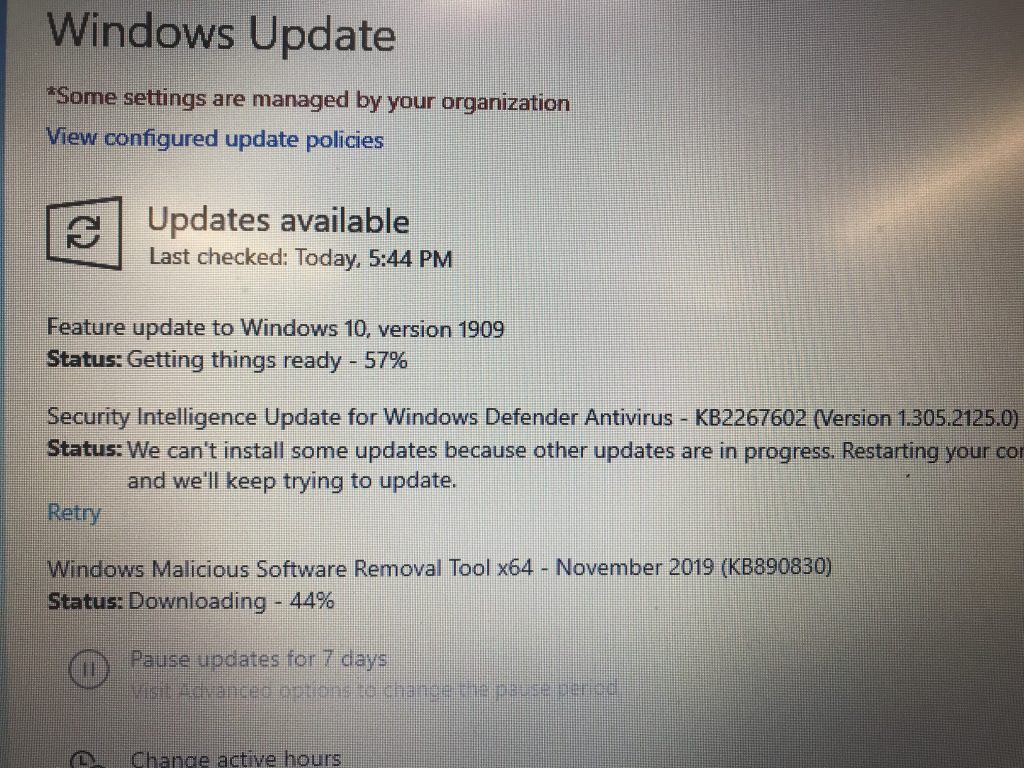
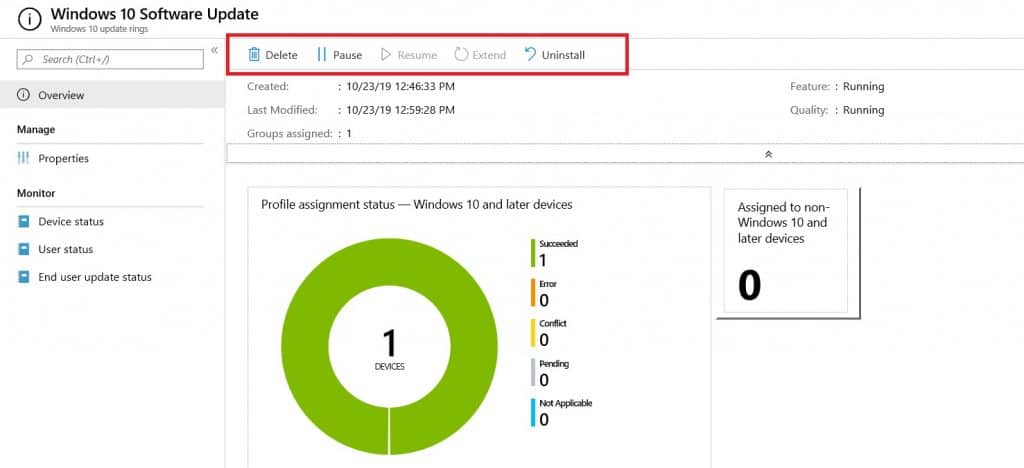
Once it’s installed, I checked in the Intune console, and I can see the following dashboard,
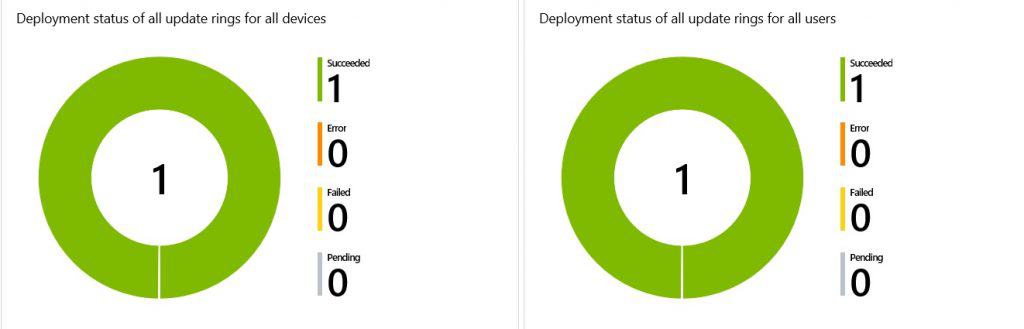
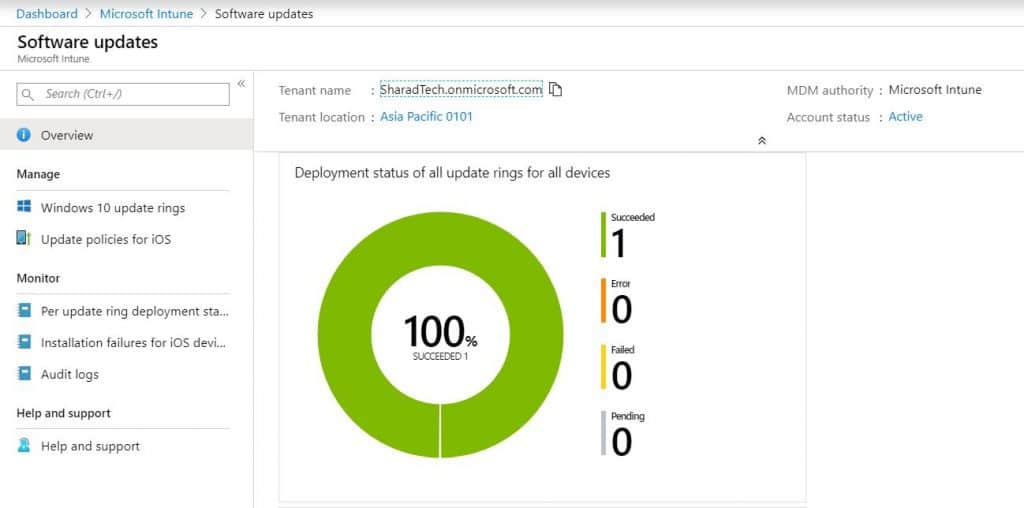
Manage Windows 10 update rings – Pause Delete Resume Extend
In the Intune portal, go to device > Windows > Windows 10 update rings > and select the policy you want to manage; you can view the status of the ring assignment.
Here you can see the following options.
- Delete
- Pause
- Resume
- Extend
Delete: Delete setting you can use if you want to remove any configured ring from Intune; while deleting, you need to under that, and deleting the ring will not remove/modify settings already assigned to the devices.
Pause: The pause setting can be used to pause any update on the device up to 35 days after the deployment.
The pause setting expires automatically after 35 days, and the device scans for applicable updates.
Resume: If you have paused any update ring, you can use this setting to resume the updates.
Extend: if any update/ring is pushed, you can use this setting to extend the pause for another 35 eds.
Resources
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Sharad has been working in the industry since 2007. Since then, he’s worked with Active Directory, Group Policy, SCCM SCOM, MS Intune, and PowerShell. Sharad currently works as a Senior Consultant in Japan. Most recently, his focus has been on SQL reporting for SCCM, MS Intune, and SCCM migration.

I have configured the updates to install at scheduled time, every day at 3am. What we encounter is that some devices still have update from september on install pending status. Next to that when in the policy we go to end User status a lot of user status have failed status. Any guidance for a good working update ring? Cause we have some updates on install pending State.
Same here and wondering the same thing. We have ours set to SAC with scheduled time at 3AM. I know several that are using surface devices and rarely restart. Curious which setting would be the best approach to remediate this pending state.
Hello Guys.
Great article. I would like to know the troubleshooting steps, to understand the update failure if any.
We have a different Win 10 Update Rings policies created and deployed to respective AAD Groups. Is there a possibility to check what policy is applied on the client, except from looking at the registry under “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Update”.
We are using WufB for quite a time now and use update compliance to analyze the trend. I could see most of the devices with Deployment Status “Unknown”, when checked for the End User Update Status for those clients in MEMCM–>Update Ring blade, the Update Status will be a failure.
I couldn’t get a possible reason for failure in Eventvwr and would be thankful if you could propose the troubleshooting steps for this. Any link to study and understand the concept better is also appriciated.
Thanks in Advance.
Will Setting Catalog Update Policy work with Update ring of Windows update for business
We have configured windows update for business by configuring the Update Ring in Intune with this we wanted to use Setting Catalog ->Windows update for business.
Will both work together?
Hi,
How can we manage Window update from Intune and SCCM at the same time?
The ConfigMgr agent sets the “specify intranet…” setting using a local group policy –the client is restricted to get the update from SCCM servers.
when we set specify intranet is not configured then client will get third-party update from SCCM or not
please Guide.
Hi,
workplace joined devices can be patched through intune
Hi there:
I would like to confirm something in the “User experience setting” section:
It states three settings within the text that are not present in the screenshot:
Require user approval to dismiss restart notification – No
Remind user before required auto-restart with a dismissible reminder (hours) – The allowed number of hours, 2, 4, 8, 12, or 24 – 2 Hours.
Remind user prior to required auto-restart with a permanent reminder (minutes) – The allowed number of minutes, 15, 30, or 60 – 30 Minutes.
I assume that this text is related to previous versions or something because is not present currently in Microsoft Intune nowadays… or are they?
I am looking for the most similar behaviour like SCCM for which a permanent dialog is shown as notification. However, tried so many configurations and read so many blogs with no luck.
Already configured as Configuration policy these two settings:
Auto Restart Notification Schedule – 240 Minutes
Auto Restart Required Notification Dismissal -> User Dismissal.
Seems not functioning as I expect. Will try also with “ScheduleImminentRestartWarning” just in case.
Said so, is there any other way to configure the permanent dialog with a previous time (1-2-3 hours) of advice before force restart?
Thanks a lot!